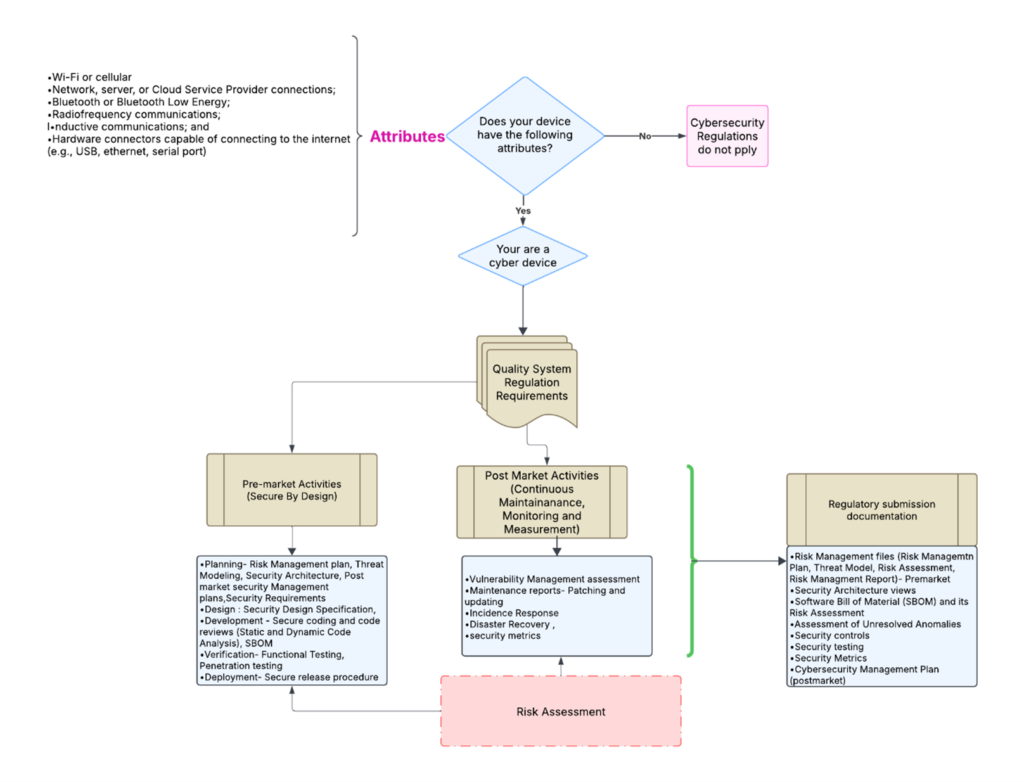
Explanation of US FDA requirements for establishing a software development lifecycle that results in secure software.
Is cybersecurity applicable to your device?
As medical devices become more connected and threats evolve, the probability of a security breach increases. To address these growing concerns, the FDA has published 2023 guidance on “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions” as an approach to strengthen the cybersecurity and safety of medical devices. The guidance requires manufacturers to integrate security as a fundamental aspect throughout the entire device lifecycle, from initial planning to decommissioning.
Your device is a cyber device if the following attributes apply
- Wi-Fi or cellular
- Network, server, or Cloud Service Provider connections.
- Bluetooth or Bluetooth Low Energy.
- Radiofrequency communications.
- Inductive communications; and
- Hardware connectors capable of connecting to the internet (e.g., USB, Ethernet, serial port)
How is secure software addressed by quality systems?
As the title of the guidance suggests, the FDA wants manufacturers to incorporate cybersecurity into their quality systems. These regulations will address both pre-market and post-market security requirements throughout the device’s life. This requirement ensures that a consistent design and labeling approach is employed throughout the industry as common practice.
- Premarket Quality system regulation requirements must incorporate security-related phases, such as:
- Planning
- Design
- Development
- Testing
- Deployment
- Post-market Quality System requirements: To maintain robust cybersecurity, the manufacturers need to focus on the following key post-market areas for monitoring and maintenance:
- Risk Management: Identify and mitigate risks by conducting regular vulnerability assessments.
- Incident Response: Prepare an incident response plan for detecting, reporting, and responding to security breaches.
- Software Updates: Regularly update and patch the software to ensure system security and integrity.
- Reporting and Communication: Establish an effective communication strategy and policy for vulnerability disclosure.
Submission Requirements for Secure Software
The documentation requirements for regulatory submission will not be developed as a standalone.
To demonstrate that your device is secure and that it has been developed following a Secure Software Development Lifecycle (SSDLC), the manufacturers must include documents from both their pre-market and post-market security processes in their regulatory submissions to the FDA. The documents commonly include planning, secure coding, comprehensive risk assessment, and continuous security monitoring and management.
The documents for the regulatory submission include the following:
- Threat Modeling
- Security Architecture
- Security risk management files
- SBOM with EOL and LOS information
- Safety and security risk Assessment of vulnerabilities in the OTS components identified in the SBOM.
- Unresolved Anomalies for security impact
- Security Metrics
- Security controls
- Security Testing
- Security labeling
The flowchart below outlines a simplified process for determining pre-market and post-market requirements. It also shows what documents must be retrieved from the manufacturer’s quality systems for the regulatory submissions.